Inbound and Outbound Email
See how to configure Outbound Email settings & learn more about Inbound Email in FL3XX
Inbound Email
FL3XX tracks responses to every email it sends, ensuring that your entire team stays informed about communications without the need for complicated shared mailboxes. This functionality is particularly beneficial in the Sales department, where it creates a dedicated message thread for each quote or booking, consolidating all related correspondence. Similarly, in the Dispatch department, it establishes a unique message thread for each flight, streamlining communication and enhancing coordination.
When FL3XX sends an email, it includes a designated reply-to address. For example, if a charter quote is sent from sales@XYZoperator.com, the customer's reply will be directed to our mail server at XYZoperator@mail.fl3xx.com. This incoming reply is processed by our system, which identifies a hidden identifier within the email body and connects it to the corresponding quote or flight. As a visual cue, a red jelly will highlight the quote or flight associated with the new email.
|
|
|
We also forward it as a notification to the original sender of the email (sales@XYZoperator.com).
Given we use a string in the body of the email, the system will not recognise a reply when the sender does a "select all" + "delete". In this case the system will not process the email, but it will still forward it to the original sender to avoid losing any communication.
Outbound Email
SPF
DKIM
DMARC
How to Configure SPF?
Set-up will be slightly different depending on which environment your FL3XX is in:
- FL3XX International (you log in to app.fl3xx.com) 🔷
- FL3XX North America (you log in to app.fl3xx.us) 🔶
1. Configure SPF
There are two potential pathways to configuring SPF:
1a. We don’t have an already-configured TXT record for our domain
1b. We already have a TXT record for our domain
Please navigate to either FL3XX International or FL3XX North America below and follow the steps:
FL3XX International (app.fl3xx.com)
🔷 1a. We don’t have a TXT record yet
Simply add a new TXT record. There are 4 fields that are important to configure.
- Type: You need to choose the type TXT. The list should contain other types like A, AAAA, CNAME, MX, etc
- Name: The name should be the name of your domain. It usually is the last part of your email address after the @
- Value: The value is a special field where we define all the authorized email servers. Add exactly this without the double-quotes “v=spf1 include:mail.fl3xx.com ~all”
- “v=spf1” means that the SPF version is 1. It’s always like this
- “include:mail.fl3xx.com” means that we allow fl3xx.com to send emails on our behalf
- “~all” means that if the email comes from anything else, it should be flagged as SPAM
🔷 Example:
- TTL: This value specifies how long the internet servers should cache this record. If you are configuring this record for the first time, we recommend 300 seconds or 5 minutes.
🔷 1b. We already have a TXT record
This procedure is easier than creating a new record. For this to work properly, simply add include:mail.fl3xx.com after the v=spf1. Make sure you keep all the information in this record and do not change anything else! It should look like this “v=spf1 include:mail.fl3xx.com …”
🔷 Example:
![]()
FL3XX North America (app.fl3xx.us)
🔶 1a. We don’t have a TXT record yet
Simply add a new TXT record. There are 4 fields that are important to configure.
- Type: You need to choose the type TXT. The list should contain other types like A, AAAA, CNAME, MX, etc
- Name: The name should be the name of your domain. It usually is the last part of your email address after the @
- Value: The value is a special field where we define all the authorized email servers. Add exactly this without the double-quotes “v=spf1 include:mail.fl3xx.us ~all”
- “v=spf1” means that the SPF version is 1. It’s always like this
- “include:mail.fl3xx.us” means that we allow fl3xx.us to send emails on our behalf
- “~all” means that if the email comes from anything else, it should be flagged as SPAM
🔶 Example:
- TTL: This value specifies how long the internet servers should cache this record. If you are configuring this record for the first time, we recommend 300 seconds or 5 minutes.
🔶 1b. We already have a TXT record
This procedure is easier than creating a new record. For this to work properly, simply add include:mail.fl3xx.us after the v=spf1. Make sure you keep all the information in this record and do not change anything else! It should look like this “v=spf1 include:mail.fl3xx.us …”
🔶 Example:
![]()
2. Test SPF configuration
FL3XX International
🔷 Domain to Verify = <your domain, e.g. abc.com>. You should see "include:mail.fl3xx.com" in the results.
FL3XX North America
🔶 Domain to Verify = <your domain, e.g. abc.com>. You should see "include:mail.fl3xx.us" in the results.
How to Configure DKIM?
1. DKIM Configuration
- Type: You need to choose the type TXT. The list should contain another type like A, AAAA, CNAME, MX, etc.
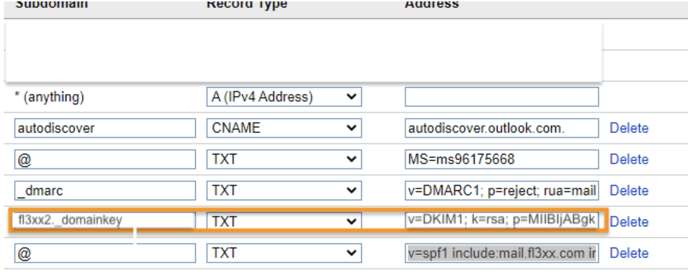
- Name: The name should always be this and pay attention to the underline: fl3xx2._domainkey
- Value: The value contains three things: a “v-tag” specifying the version, a “k-tag” specifying the type of encryption key used, and a “p-tag” containing the public key of the message signature. The exact value you need to add is displayed below:
v=DKIM1; k=rsa; p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAzO4/puhH+25v3T2iHQJJSxDbTmxe1mv8Z2CTF+vF70q1Qvhl0fNkLIH5BhRUKacOuql3u4paeufmL8zRqNCT8ge7w3mnJmcieKGeNRX5/o6MvO04Hfmmt7UWOjO7JFlPskTL12UINVXKyVsSjaSQH2bg3ZaS6SlGCxEf9qcB/+LlMu4SwNRQ+JFmw7GvQ4njIuE+/S4H0zGDB6qu7hj2mgYLox9oH3m4E4+yKuR5a6MmOuE0pGIDCz4yp8i5p7Bq0dbnqF4wQbbYD99JoXm8iPr4DGsliaWO4xpTGr3ziH/0zn2Roxxim+aOwaQRvFLjlyPaKq8AVBtZKenKrCfGhQIDAQAB;
2. Test DKIM configuration
How to Configure DMARC?
DMARC is a very powerful system, that gives you full control over how the receiving party processes your emails. You can read more here.
In this tutorial, we’re not going into detail, but we show you how to initialize your DMARC entry, which for most SPAM filters is already enough to increase your score.
1. DMARC Configuration
The DMARC configuration is similar to the SPF. This means that we will need to add a TXT record but with different values.
- Type: You need to choose the type TXT. The list should contain another type like A, AAAA, CNAME, MX, etc
- Name: The name should always be this and pay attention to the underline: _dmarc
- Value: In our basic version the value contains two things: a “v-tag” specifying the version, and a “p-tag” specifying the policy deployed by the receiving party. The exact value you need to add is displayed below:
- “v=DMARC1; p=none”
- TTL: This value specifies how long the internet servers should cache this record. If you are configuring this record for the first time, we recommend 300 seconds or 5 minutes.
2. Test DMARC configuration
After configuration, please make sure that the DMARC record is correct. Please note that changes to the DNS can take several minutes up to hours to take effect!
You can verify the DMARC configuration with for example DMARC Analyzer.
Domain to Verify = <your domain, e.g. abc.com>. Good if you see anything here. However, DMARC is an optional thing and has way less impact than the other two (SPF and DKIM).
You can also use a tool called Dig using the following command: dig +short _dmarc.[your domain, e.g. cbs.com] TXT
SMIME Certificate
In addition to the DNS improvements described above, FL3XX offers the option to sign outgoing emails with an SMIME certificate.
Mail Relay
If required by the customer, FL3XX can relay outgoing emails via the mail server of the customer.
FL3XX International
🔷 Authentication is possible based on hostname (Staging IP: 3.71.154.121 / 2a05:d014:8af:3400:355b:500e:8d68:2ca3, Production IP: 52.29.179.130 / 2a05:d014:9a:1801:9304:ce7a:d7c6:3440 )or login credentials.
FL3XX North America
🔶 Authentication is possible based on whitelisting (Staging IP: 184.169.249.43 / 2600:1f1c:974:8700:5af9:9397:4188:c911, Production IP: 54.193.219.134 / 2600:1f1c:b07:4400:78a2:1bb:9150:3772) or login credentials.
Please contact FL3XX Support with your Mail-Server URL/IP-Address and authentication details to set this up.
Conclusion
After setting up the SPF, DKIM, and DMARC records, FL3XX will be able to send emails on your behalf to your customer with a better reputation score. You can test the score online with MailTester. You can create a dedicated email address there and send an email directly from FL3XX to this email. Currently, our score should be in the area of 9, which is an excellent result.
This will ensure those emails won’t end up in the SPAM folder. In any case, if you are not sure what you are doing, we can assist you in the configuration of those settings.
Signing emails with an SMIME Certificate aims to increase the trustworthiness of outgoing emails.
Implementing one's own mail relay is not recommended for standard users.
You can also download the PDF files here:

 Red jelly shown in Dispatch
Red jelly shown in Dispatch